Kode Syair HK Hari Ini - Forum Syair Hongkong - Syair HK






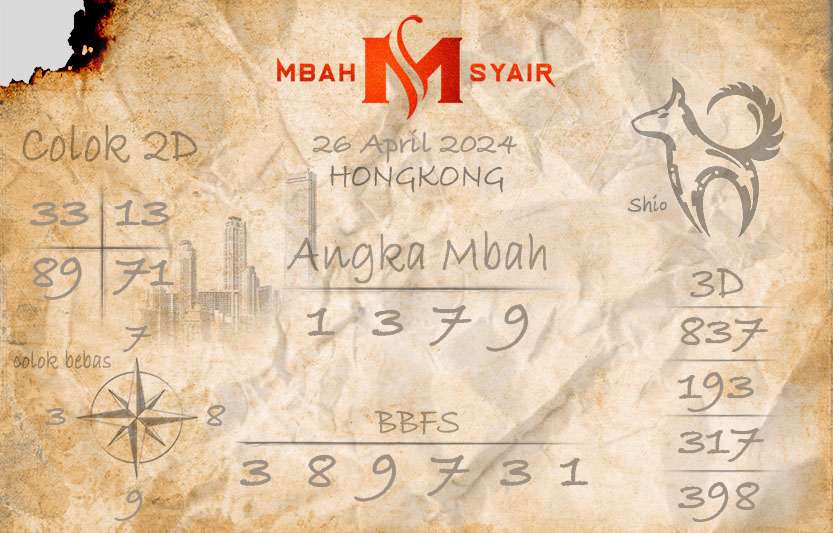







Kode Syair HK Hari ini merupakan platform di mana para pemain togel Hongkong dapat memperoleh syair, gambar-gambar, atau sonji untuk meracik angka-angka tepat dalam taruhan togel HK. Situs ini menjadi sumber informasi yang sangat dicari, terutama bagi para penggemar togel Hongkong. Gambar-gambar terkait togel HK sangat populer di kalangan pemain togel, khususnya mereka yang bermain di Hongkong.
LIVE DRAW HONGKONG
Live HK adalah portal yang khusus menyediakan siaran langsung hasil keluaran togel Hongkong dan telah terhubung langsung ke situs utama Hongkongpools.com
Para pemain togel online seringkali mengalami kesulitan dalam mengakses situs resmi keluaran togel HK yang telah diblokir oleh sistem Nawala di Indonesia. Oleh karena itu, kami dengan cepat menciptakan situs Live HK yang dapat diakses secara gratis oleh para penggemar togel Hongkong tanpa perlu khawatir akan terkena internet positif.
Live Draw Hongkong hari ini sangat penting bagi para pecinta togel HK karena informasi yang disajikan dapat memberikan gambaran tentang angka jackpot prize 1, prize 2, dan prize 3 yang tersedia dalam pengeluaran HK.
Live Draw HK akan selalu menampilkan hasil keluaran togel Hongkong setiap harinya secara langsung sesuai dengan jadwal yang telah ditetapkan. Sebagai contoh, Hongkong Pools biasanya tidak mengeluarkan hasil atau libur pada hari Selasa dan Jumat. Live Draw Togel Hongkong biasanya dimulai pada pukul 17:37 WIB dan berlangsung hingga pukul 18:05 WIB pada sore hari.
Live Result HK / Hongkong / Hongkong dapat Anda saksikan langsung sesuai dengan jadwal yang telah ditentukan, yakni mulai pukul 17:37 WIB hingga pukul 18:05 WIB. Kami berharap angka yang Anda pasang akan muncul dalam tabel keluaran Live HK yang tersedia di bawah ini.
Result HK
Berikut adalah informasi penting mengenai Syair yang dapat kami berikan kepada Anda. Selain menyajikan hasil keluaran Kode Syair, Syair HK juga memiliki situs serupa untuk pasaran lain seperti Hongkong, Hongkong, dan Hong Kong. Anda dapat mengakses situs-situs tersebut dengan mengklik menu yang tersedia di bagian atas halaman.
Link Yang Berkaitan :
SYAIR HK OPESIA | SYAIR HK VIP | SYAIR HK
Copyright © 2024 Syair HK Terlengkap All rights reserved.